WEBSITE 2 DESIGN


Security Researcher Rafie Muhammad reported a reflected Cross-Site Scripting (XSS) vulnerability to Wordfence that they discovered in Download Manager, a WordPress plugin installed on over 100,000 sites. On request, we assigned a vulnerability identifier of CVE-2022-1985, on May 30, 2022.
Even though Wordfence provides protection against this vulnerability, we strongly recommend ensuring that your site has been updated to the latest patched version of Download Manager, which is version 3.2.43 at the time of this publication.
Affected Plugin: Download Manager
Plugin Slug: download-manager
Description: Reflected Cross-Site Scripting
Affected Versions: <= 3.2.42
Plugin Developer: codename065
CVE ID: CVE-2022-1985
CVSS Score: 6.1 (Medium)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Researcher/s: Rafie Muhammad (Yeraisci)
Fully Patched Version: 3.2.43
Download Manager is a file and document management plugin to help manage and control file downloads with various file download controls to restrict unauthorized file access.
Download Manager plugin also provides a complete solution to sell digital products from WordPress sites, including checkout functionality to complete an order. One feature of the plugin is the ability to use a shortcode to embed files and other assets in a page or post. This function was found to be vulnerable to reflected Cross-Site Scripting.
Secure coding practices would include checks to sanitize the input received by the page, and escaping that code on the output to ensure that only approved inputs and outputs are presented.
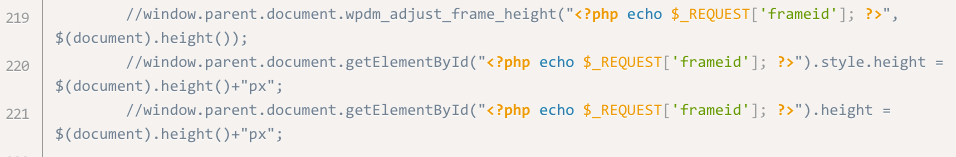
Unfortunately, insufficient input sanitization and output escaping on the $_REQUEST[‘frameid’] parameter found in the ~/src/Package/views/shortcode-iframe.php file of the Download Manager plugin made it possible for an attacker to run arbitrary code in a victim’s browser by getting them to click on a specially crafted URL. This is because the ‘frameid’ parameter was echoed to the page without sufficient user input validation.
Without proper sanitization and escaping in place on user-supplied inputs, JavaScript can be used to manipulate the page. Even an unsophisticated attacker could hijack the form and use it to trick a site administrator into unknowingly disclosing sensitive information, or to collect cookie values.
More specialized attackers would use this capability to gain administrator access or add a backdoor and take over the site. If the attacker gains this access, they would have access to the same information the administrator would be able to access, including user details and customer information.
In the case of Download Manager, access and customer information to digital products would both be at risk. If an attacker were able to trick an administrator into clicking a link that has been designed to implement a backdoor on the website or send session cookies to the attacker, add a malicious administrator account, the attacker would also have free reign in the administrator panel, giving them the ability to modify checkout settings and even add fake products to the website.
It is recommended, that you always have a backup of your website daily or weekly so that it will be easy to revert it back to the clean version to avoid getting into the worst malware case. Please update the Download Manager Plugin to the latest Patched version which is v3.2.43
Read Other Posts: How to update your WordPress theme for Beginners
And: Is Image Alt Text Important For SEO?
Website2Design will help you clean your hacked WordPress website and also help you with regular web security so that you can focus more on your business than your website.